Malicious Code Is Best Described as
In a tweet Affable Kraut also reported another similar obfuscation. Find one that best meets your needs and budget and run it regularly to help reduce the risk of malware infection and limit the impact of code compromise.

What Is Malicious Software Different Types Of Malicious Software
Malicious code can do damage by corrupting files erasing your hard drive andor allowing hackers access.

. A security analyst has a sample of malicious software and needs to know what the sample does. It is code not easily or solely controlled through the use of anti-virus tools. The technical name for a virus also known.
It could best be described as a glorified grep script plus an aggregation of other open-source tools. Dubbed AF91 the virus is designed to exploit highly protected command and control systems. Unfortunately malicious code cannot be efficiently managed by conventional antivirus software.
Cleaning computer components C. November 2 2020 Denis Sinegubko. Code thats intended to damage a computer or steal information.
This Practice falls under the second Capability within the SI Domain C041 Identify Malicious Content and can be found in the CMMC Appendix B page B-238 Page. A logic bomb is malware that executes in response to an event such as a specific date and time. Static analysis for PHP.
Malicious code includes viruses Trojan horses worms macros and scripts. Malicious code can either activate itself or be like a virus requiring a user to perform an action such as clicking on something or opening an email attachment. CSS-JS Steganography in Fake Flash Player Update Malware.
Forensic examination of Windows systems is an important part of analyzing malicious code providing context and additional information that helps in understanding the functionality and origin of MalwareTrace evidence relating to a particular piece of Malware is found in the operating systems and file. And other tools based on Linux grep command. WordPress plugins can detect malicious code and safeguard your site from potential threats.
Any code in a software system or script intended to cause undesired effects security breaches or damage to a system. Malicious code can be spread by e-mail attachments downloading files and visiting infected websites. A software virus developed by the best programmers at NSA to target real-time computer systems.
Since current applications tend to be designed and built more and more often with reusable components from a variety of sources with varying levels of security malicious code can pose. The approach of malware analysis can BEST be described as. However for this article the term is being applied to static code and not morphing codes which were discussed in a previous article.
Aquilina in Malware Forensics 2008 Publisher Summary. What is malicious code. Computer worm - 16451290.
For clarity malicious code is globally used as an umbrella term for all types of malevolent program code. Fundamentally malicious code families are initially comprised of one or more distinct malicious code samples. In order to perform static plugin source code audit the following tools can be used.
John Gantzs April 1 1991 column in. Malicious code is a term that describes the code thats used in online forms scripts and software that aims to cause harm in some way. Using Malicious Computer Code as a Weapon.
Described a new and awesome weapon. System resources are stretched thin as the size of the signature database grows severely affecting performance and negating any performance gains from the stream-based methods. Malicious code or malcode is any code that has been intentionally designed to cause harm or undesired effects in a software system.
Ransomware takes control of a users computer or data and demands a ransom to return control to the user. This scenario describes CryptoLocker. The analyst runs the sample in a carefully-controlled and monitored virtual machine to observe the softwares behavior.
This summer MalwareBytes researcher Jérôme Segura wrote an article about how criminals use image files ico to hide JavaScript credit card stealers on compromised e-commerce sites. Worms infect computers over a network and while. To help your employees avoid the risks associated with downloading and installing malicious code here are some helpful tips.
We now explore the 2nd Practice within the Domain System and Information Integrity SI SI211 - Provide protection from malicious code at appropriate locations within organizational information systems. What is malicious code. Why is it difficult to protect against.
Malicious code describes a broad category of system security threats that include typical attack scripts viruses worms Trojan horses backdoors and malicious active content. This post was originally published in January 2020 and has been updated for comprehensiveness. Malicious Code DetectionStopping Malware at the Gateway A Fortinet White Paper and the mutated variants can increase to unrealistic proportions.
A malicious program that is disguised as or embedded within legitimate software. Malicious code is code causing damage to a computer or system. A static source code analyzer for vulnerabilities in PHP scripts.
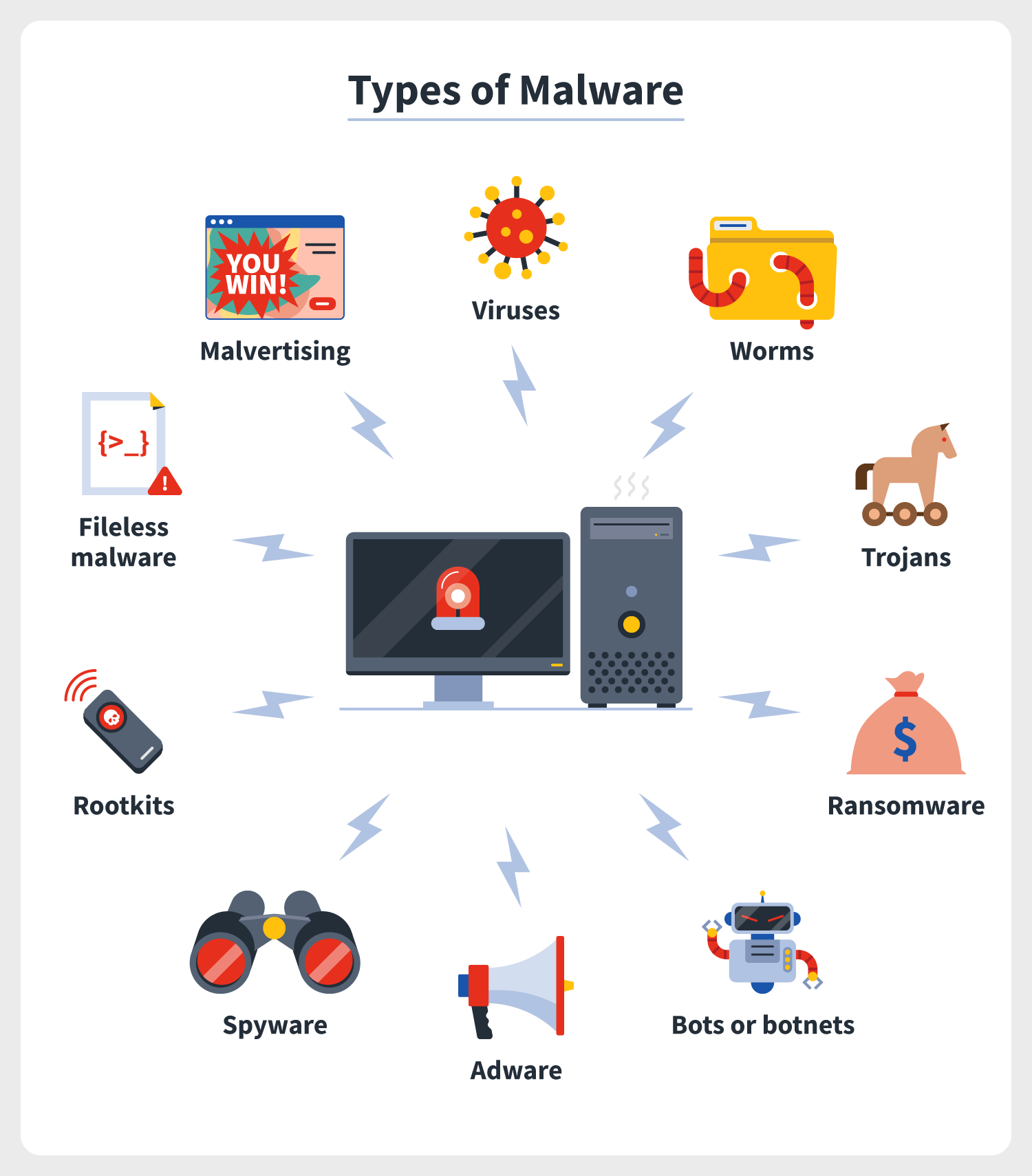
10 Types Of Malware How To Prevent Malware From The Start Norton

The Term Ransom Has Been Around For Hundreds Of Years And Is Best Described As Computer Security Cyber Security Education Cyber Security Awareness

Is Your Data Secure 4 Tips How To Stay Safe Against Ransomware Cyber Security Technology Cyber Security Education Cyber Security Awareness
No comments for "Malicious Code Is Best Described as"
Post a Comment